In today’s digital world, Wireshark is a powerful tool used by network administrators and security analysts. It helps them understand and manage networks better by capturing and examining network packets. One essential feature of Wireshark is filtering by IP addresses, which allows professionals to focus on specific sources and destinations of traffic. In this article, we will explore how to filter by IP in Wireshark, from basic filtering by source and destination IP addresses to more advanced techniques like using IP address ranges. Let’s begin our journey into the world of Wireshark’s IP filtering!
Filtering by Source IP Address
First you must open Wireshark and start capturing packets. I am using a wireless connection, so I will select the ‘Wi-Fi’ option to start capturing packets.

Locate the filter bar at the top of the Wireshark window, then type ‘ip.src’ followed by ‘==’ and the desired IP address. Here’s an example with the IP address 10.0.0.51:
ip.src == 10.0.0.51The filter bar will be highlighted green if the syntax is valid. Press Enter to apply the filter. This will cause Wireshark to display only the packets whose source is 10.0.0.51.

You can see that all of the displayed packets have 10.0.0.51 as their source.
Filtering by Destination IP Address
To filter by destination IP, simply use ‘ip.dst’ as shown below.
ip.dst == 10.0.0.51Applying this filter will show all packets whose destination matches the IP address 10.0.0.51.
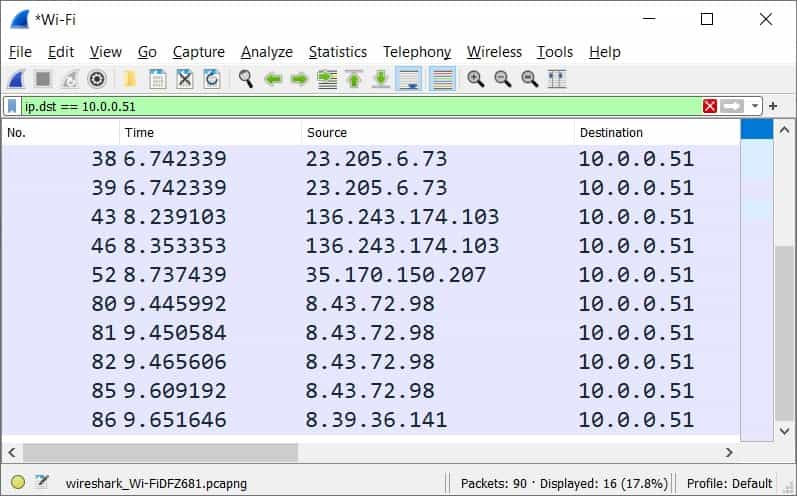
As expected, Wireshark displayed all the packets whose destination is 10.0.0.51.
Filtering by Either Source or Destination
If you wish to filter packets that have a specific IP address either as the source or the destination, you can use the following display filter:
ip.addr == 10.0.0.51By applying this filter, Wireshark will display packets where either the source or destination IP address matches 10.0.0.51. This approach is particularly useful when you need to analyze traffic associated with a particular IP address, regardless of whether it acts as the sender or receiver in the communication.

You can see that the address 10.0.0.51 is present in either the source column or the destination column for each packet.
Combining Source and Destination IP Filters
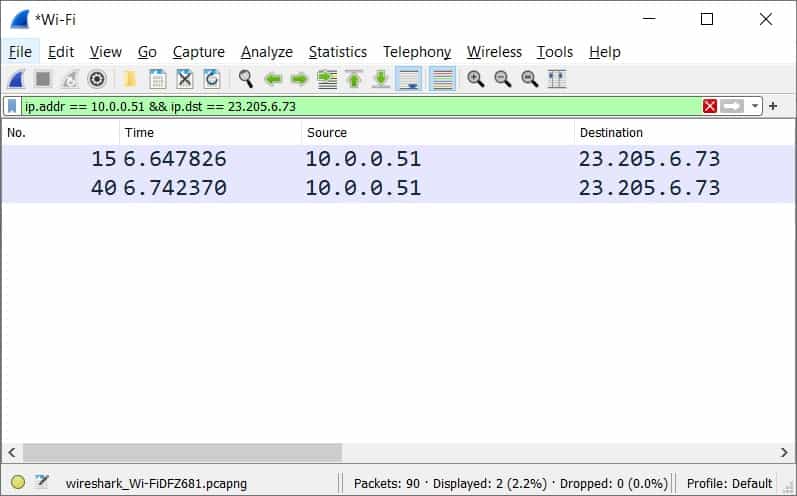
To analyze packets with specific source and destination IP addresses simultaneously, you can combine filters using the ‘&&’ operator. Here’s an example:
ip.src == 10.0.0.51 && ip.dst == 23.205.6.73By applying this filter, Wireshark will show packets where the source IP is 10.0.0.51 and the destination IP is 23.205.6.73. This method helps you pinpoint network traffic between two particular IP addresses.
Filtering by IP Address Range
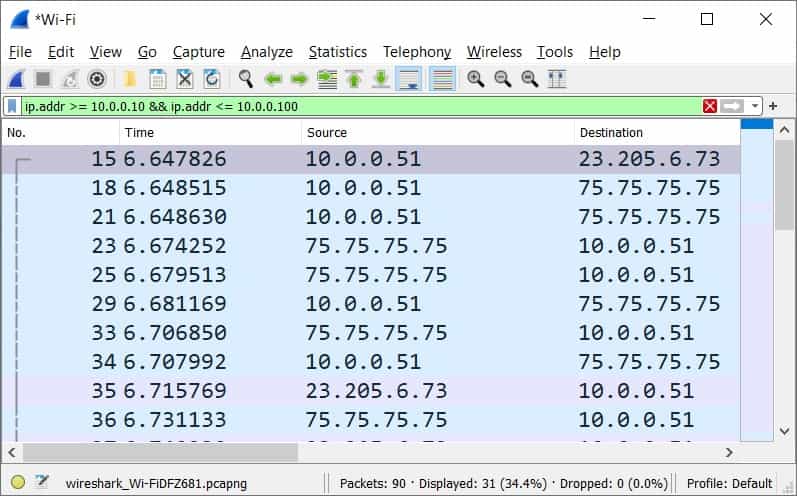
Operators can be used to filter by a range of addresses. This can be done with a display filter like this:
ip.addr >= 10.0.0.0 && ip.addr <= 10.0.0.100By applying this filter, Wireshark will show packets whose source or destination IP address falls within the range of 10.0.0.0 to 10.0.0.100. This is a useful technique when you need to narrow down your analysis to a specific segment of IP addresses within your network.
Excluding an IP Address
You can exclude a specific IP Address by using the following display filter:
!(ip.addr == 10.0.0.51)By applying this filter, Wireshark will only show packets where the source and destination IP addresses are not 10.0.0.51. This is helpful when you want to focus on all network traffic except for that specific IP address.
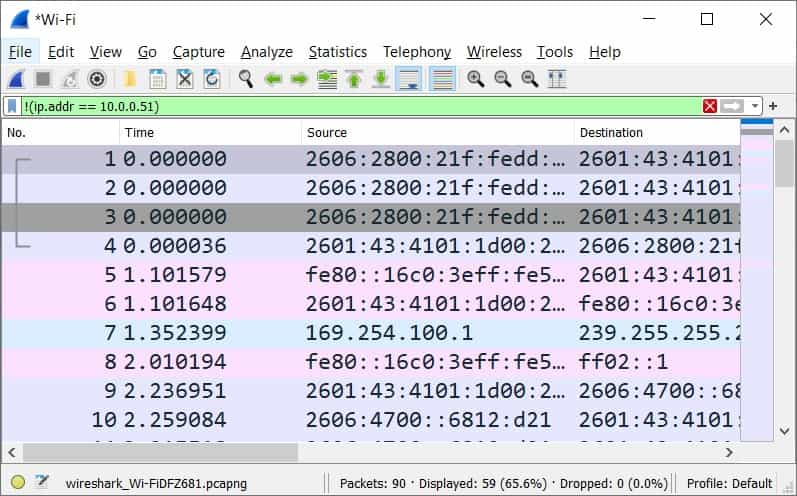
You can see that Wireshark displayed all packets without the address 10.0.0.51.
Conclusion
Mastering IP filtering in Wireshark empowers network professionals to focus on relevant data, swiftly troubleshoot issues, and enhance security. By harnessing the tool’s display filters, users can extract valuable insights from network packets, leading to more informed decisions and optimized network performance. With this essential skill, Wireshark becomes an indispensable asset in the pursuit of efficient and secure network analysis. To learn more about Wireshark, read the official documentation.

